Showing posts with label Packet Tracer Tutorial. Show all posts
Showing posts with label Packet Tracer Tutorial. Show all posts
March 31, 2013
December 10, 2012
Voice over IP (VOIP) on packet tracer
Voice over IP (VoIP, or voice over Internet Protocol) commonly refers to the communication protocols, technologies, methodologies, and transmission techniques involved in the delivery of voice communications and multimedia sessions over Internet Protocol (IP) networks, such as the Internet. Other terms commonly associated with VoIP are IP telephony,Internet telephony, voice over broadband (VoBB), broadband telephony, IP communications, and broadband phone.
Internet telephony refers to communications services —voice, fax, SMS, and/or voice-messaging applications— that are transported via the Internet, rather than the public switched telephone network (PSTN). The steps involved in originating a VoIP telephone call are signaling and media channel setup, digitization of the analog voice signal, encoding, packetization, and transmission as Internet Protocol (IP) packets over a packet-switched network. On the receiving side, similar steps (usually in the reverse order) such as reception of the IP packets, decoding of the packets and digital-to-analog conversion reproduce the original voice stream. Even though IP telephony and VoIP are used interchangeably, IP telephony refers to all use of IP protocols for voice communication by digital telephony systems, while VoIP is one technology used by IP telephony to transport phone calls
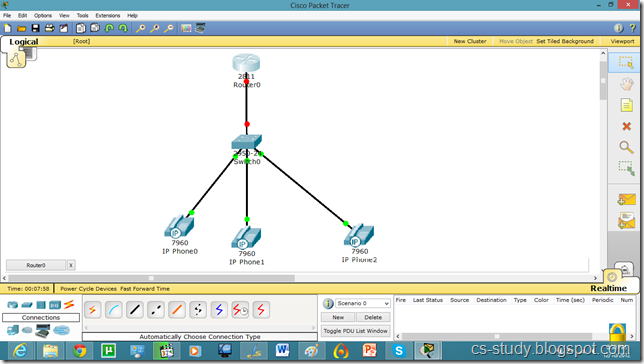
Let us apply it on packet tracer.
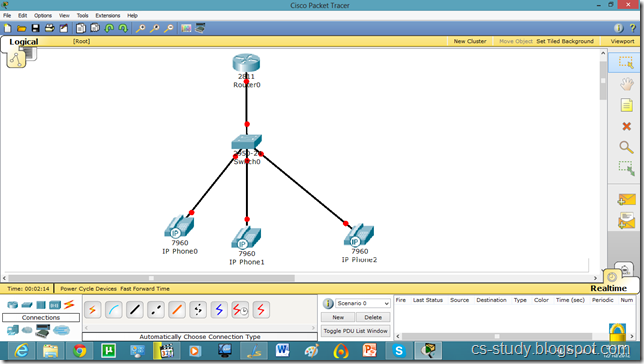
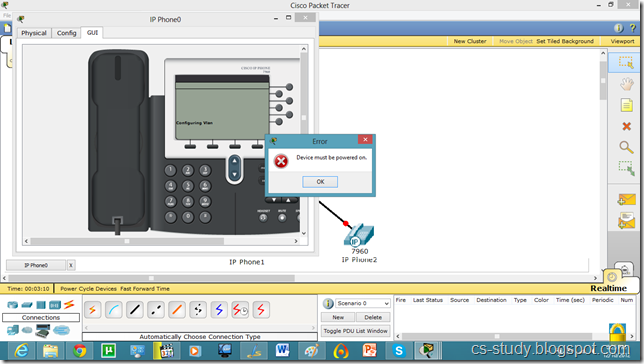
This IP Phone is displayed below. And when we try to go to any other mode its give us error and ask us to switch it on first.
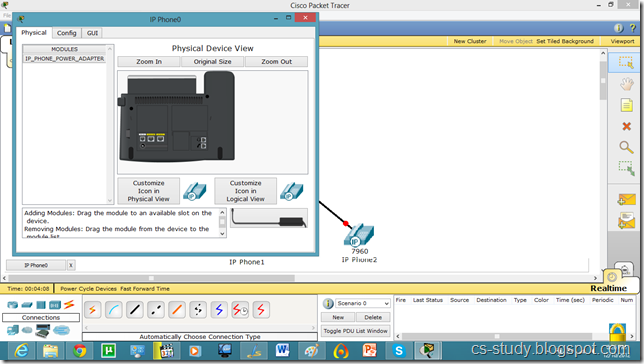
For that, go to Physical mode and put the power adapter (in the bottom right corner) into the phone as shown in figure.
Now, we have inserted the antenna into IP phone. Repeat it for other phones as well.
Now, we see that interface of IP phone is UP.
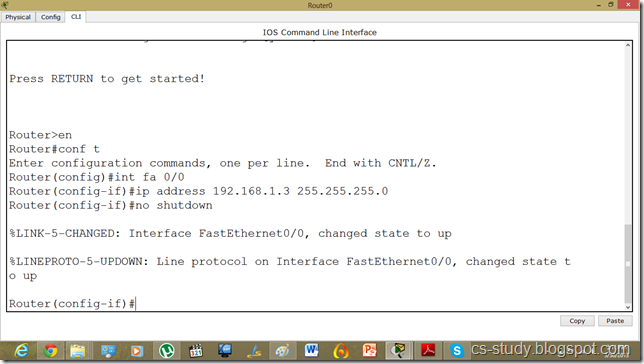
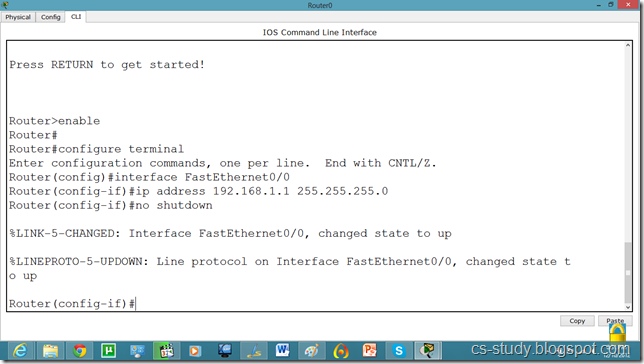
Now, go to router and assign IP address.
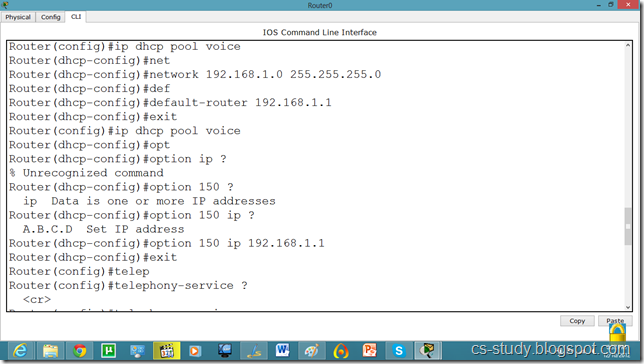
We will have to set DHCP server on router to assign IP addresses to IP phones.
We will have to give an additional command for voip.
Router(dhcp-config)#option 150 ip 192.168.1.1
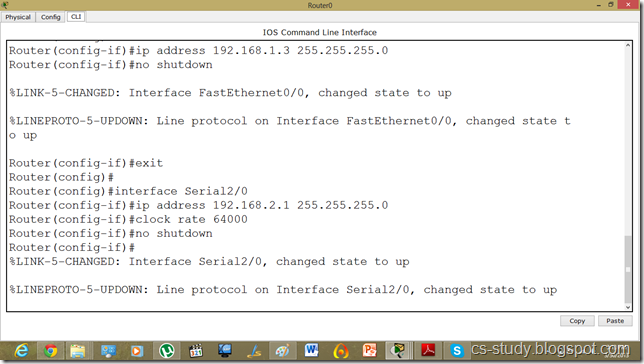
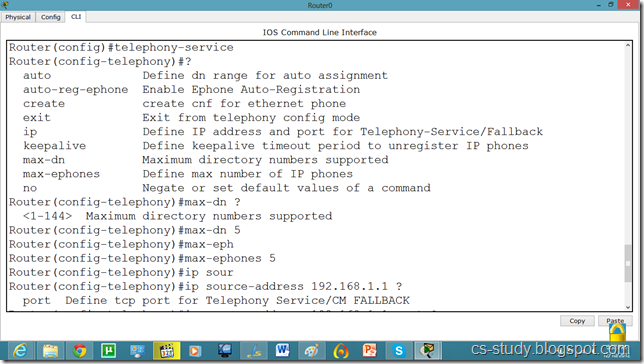
Now, let us apply commands to the router for voip. You might have noticed we took 2811 series router because it facilitates the following commands.
Continued.
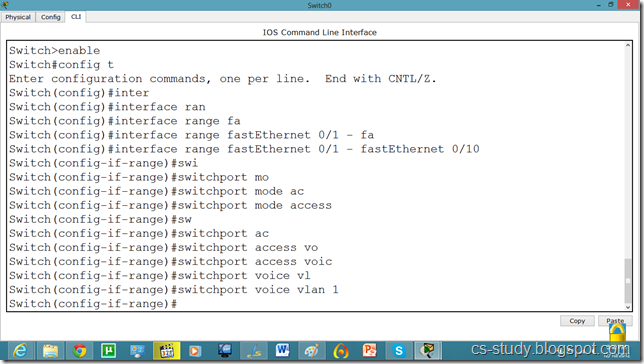
Now, we will go to the switch and make the interfaces support voip as follows.
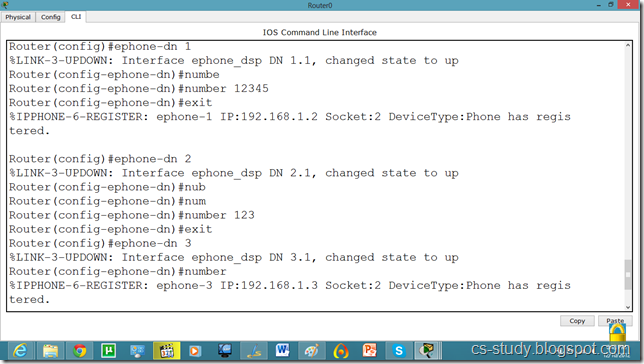
After that, we will have to assign phone number to our IP phone by applying following commands.
Continued…
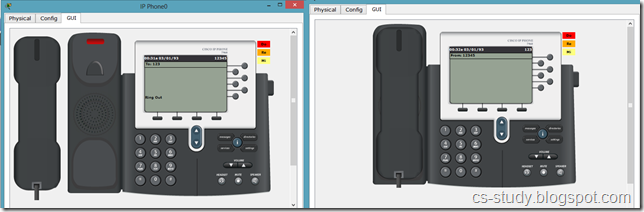
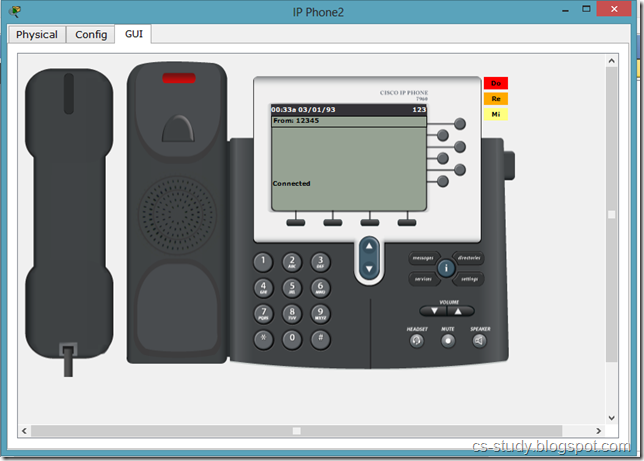
Now, we can see that in GUI mode of Phone, we have a phone number available.
This means that we can call from one phone to the other. Lets do that.
And when we pick up the reciever, it says that we are connected :) .
Commands on Router for VOIP
Router(config)#ip dhcp pool voice
Router(dhcp-config)#option 150 ip 192.168.1.1
Router(dhcp-config)#exit
Router(config)#telephony-service
Router(config-telephony)#max-dn 5
Router(config-telephony)#max-ephones 5
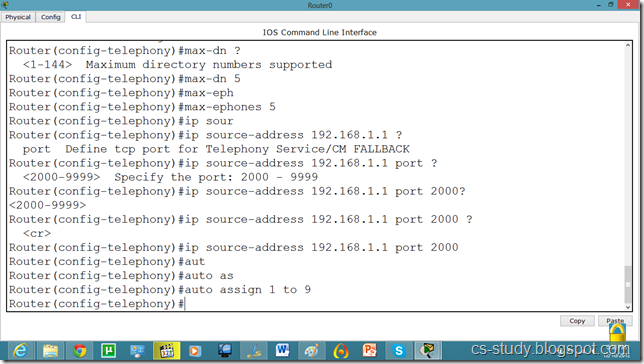
Router(config-telephony)#ip source-address 192.168.1.1 port 2000
Router(config-telephony)#auto assign 1 to 9
Router(config-telephony)#exit
Router(config)#ephone-dn 1
%LINK-3-UPDOWN: Interface ephone_dsp DN 1.1, changed state to up
Router(config-ephone-dn)#number 12345
Router(config-ephone-dn)#exit
Router(dhcp-config)#option 150 ip 192.168.1.1
Router(dhcp-config)#exit
Router(config)#telephony-service
Router(config-telephony)#max-dn 5
Router(config-telephony)#max-ephones 5
Router(config-telephony)#ip source-address 192.168.1.1 port 2000
Router(config-telephony)#auto assign 1 to 9
Router(config-telephony)#exit
Router(config)#ephone-dn 1
%LINK-3-UPDOWN: Interface ephone_dsp DN 1.1, changed state to up
Router(config-ephone-dn)#number 12345
Router(config-ephone-dn)#exit
%IPPHONE-6-REGISTER: ephone-1 IP:192.168.1.2 Socket:2 DeviceType:Phone has registered.
Router(config)#ephone-dn 2
%LINK-3-UPDOWN: Interface ephone_dsp DN 2.1, changed state to up
Router(config-ephone-dn)#number 123
Router(config-ephone-dn)#exit
Router(config-ephone-dn)#number 123
Router(config-ephone-dn)#exit
Router(config)#ephone-dn 3
%LINK-3-UPDOWN: Interface ephone_dsp DN 3.1, changed state to up
Router(config-ephone-dn)#number 11111
Router(config-ephone-dn)#exit
%LINK-3-UPDOWN: Interface ephone_dsp DN 3.1, changed state to up
Router(config-ephone-dn)#number 11111
Router(config-ephone-dn)#exit
Commands on Switch for VOIP
Switch(config)#interface range fastEthernet 0/1 - fastEthernet 0/10
Switch(config-if-range)#switchport mode access
Switch(config-if-range)#switchport voice vlan 1
Switch(config-if-range)#switchport voice vlan 1
December 9, 2012
Telnet and SSH on packet tracer
A terminal emulation program for TCP/IP networks such as the Internet. The Telnet program runs on your computer and connects your PC to a server on the network. You can then enter commands through the Telnet program and they will be executed as if you were entering them directly on the server console. This enables you to control the server and communicate with other servers on the network. To start a Telnet session, you must log in to a server by entering a valid username and password. Telnet is a common way to remotely control Web servers. To telnet means to establish a connection with the Telnet protocol, either with command line client or with a programmatic interface.
SSH
Secure Shell (SSH) is a cryptographic network protocol for secure data communication, remote shell services or command execution and other secure network services between two networked computers that connects, via a secure channel over an insecure network, a server and a client (running SSH server and SSH client programs, respectively). It was designed as a replacement for Telnet and other insecure remote shell protocols such as the Berkeley rsh and rexec protocols, which send information, notably passwords, in plaintext, rendering them susceptible to interception and disclosure using packet analysis. The encryption used by SSH is intended to provide confidentiality and integrity of data over an unsecured network, such as the Internet.
a network protocol that ensures a high-level encryption, allowing for the data transmitted over insecure networks, such as the Internet, to be kept intact and integrate. SSH and SSH Telnet, in particular, work for establishing a secure communication between two network-connected computers as an alternative to remote shells, such as TELNET, that send sensitive information in an insecure environment.
In contrast to other remote access protocols, such as FTP, SSH Telnet ensures higher level of connection security between distant machines but at the same time represents a potential threat to the server stability. Thus, SSH access is considered a special privilege by hosting providers and is often assigned to users only per request.
Let us apply Telnet and SSH on packet tracer.
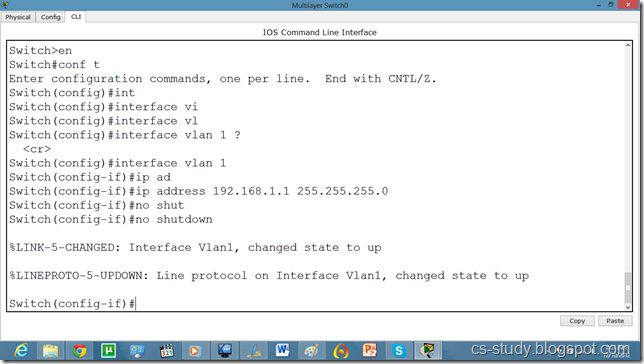
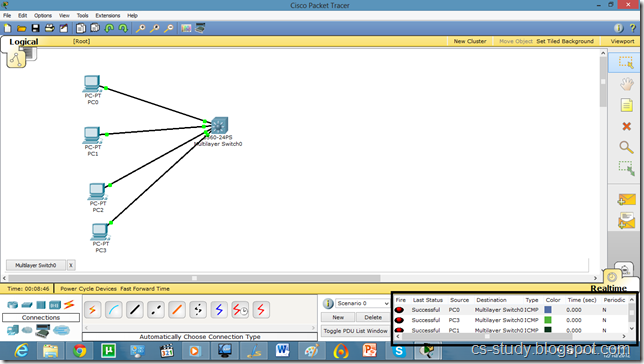
Take the topology as in the above diagram. Set IPs on the PCs. As, by default, all PCs are in vlan 1. We will create a virtual interface on switch with vlan 1 as follows.
Now, we can ping to switch by our hosts because hosts are in vlan 1 and switch also has a vlan 1 interface.
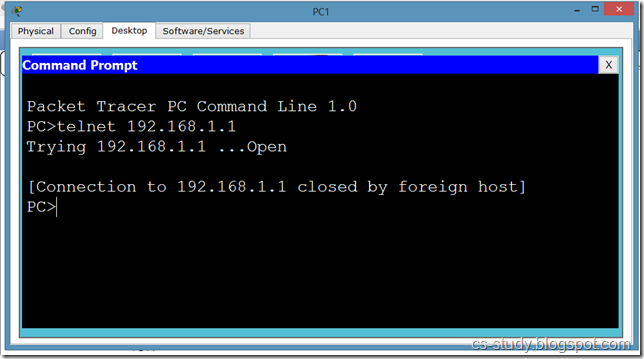
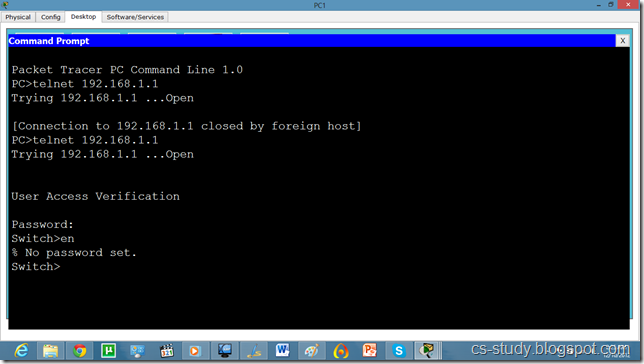
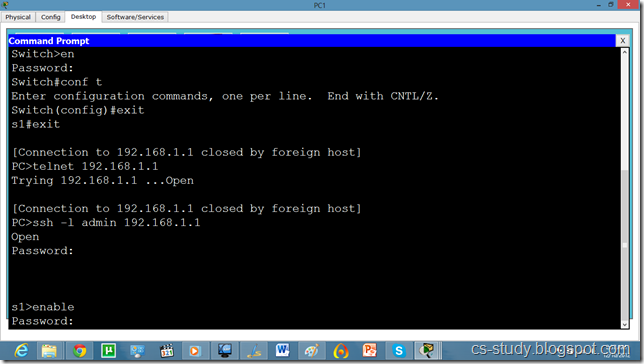
Now, try to telnet the switch from our PC, it refuses because we have not applied authentication on the switch yet.
So, lets apply line authentication on the switch. The system supports 20 virtual tty (vty) lines for Telnet, Secure Shell Server (SSH) and FTP services. Each Telnet, SSH, or FTP session requires one vty line. You can add security to your system by configuring the software to validate login requests.
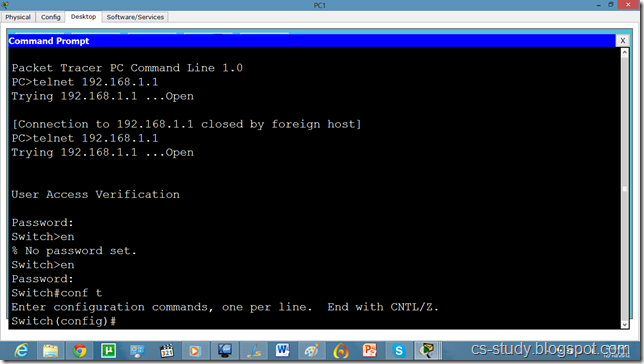
Now, we can easily telnet. But it does not let us go in the switch enabled mode because we have not set the password on the switch yet.
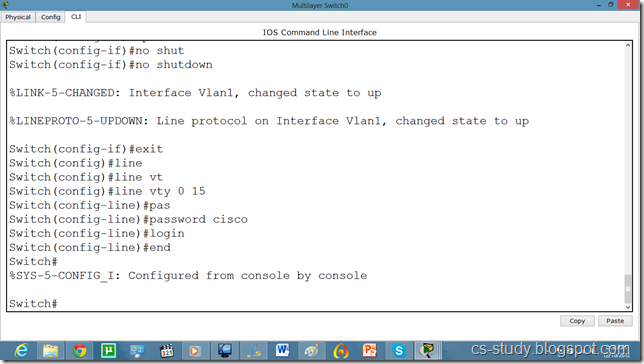
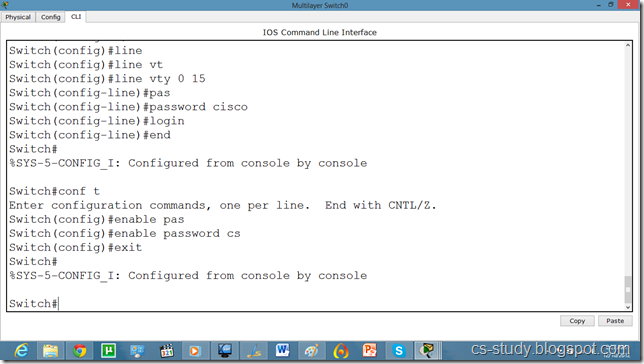
Lets apply password on the switch enabled mode.
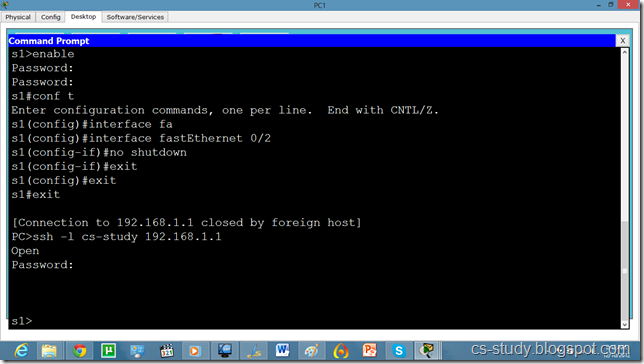
Now, we can go inside Switch configuration mode from our pc.
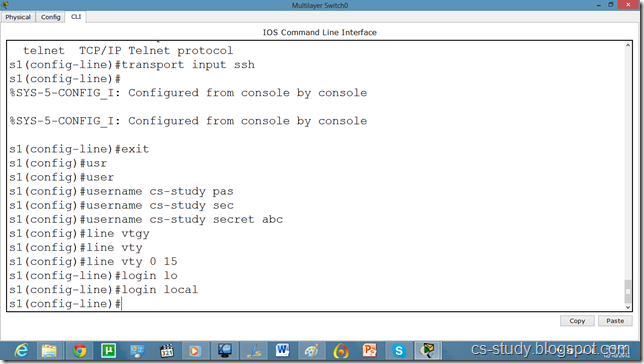
So, now let us apply SSH on the switch.
Commands continued.
Now, we try to telnet it but it is refused because ssh has over ruled telnet. So, we will use SSH protocol on it. By default username is admin.
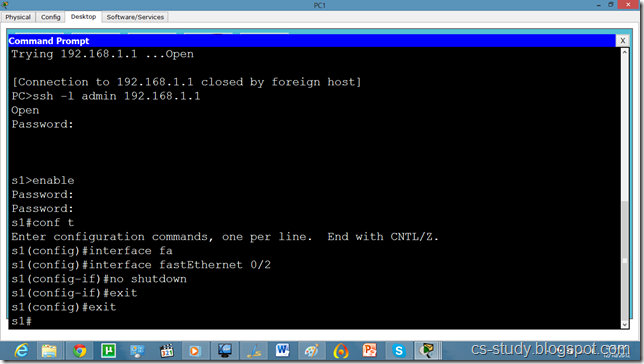
And we can apply any sort of configuration on our switch from out pc.
Now, if we want to change the username from admin to something else, we will do it as follows.
and from our pc as follows.
The SSH commands are as follows.
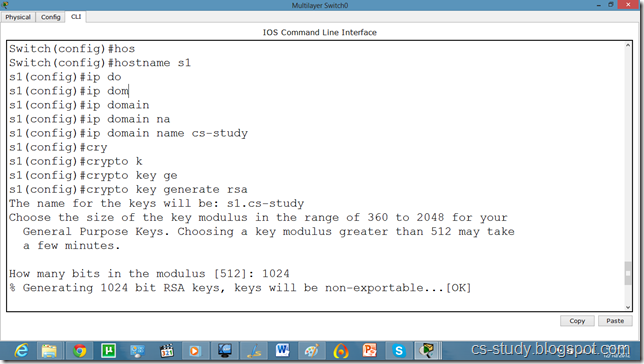
Switch(config)#ip domain name ?
WORD Default domain nameSwitch(config)#ip domain name abc.comSwitch(config)#crypto key generate rsa
% Please define a hostname other than Switch.
Switch(config)#hostname s1
s1(config)#ip domain name cs-studys1
s1(config)#crypto key generate rsa
Choose the size of the key modulus in the range of 360 to 2048 for your General Purpose Keys. Choosing a key modulus greater than 512 may take a few minutes.
s1(config)#line vty 0 15
s1(config-line)#transport input ssh
WORD Default domain nameSwitch(config)#ip domain name abc.comSwitch(config)#crypto key generate rsa
% Please define a hostname other than Switch.
Switch(config)#hostname s1
s1(config)#ip domain name cs-studys1
s1(config)#crypto key generate rsa
Choose the size of the key modulus in the range of 360 to 2048 for your General Purpose Keys. Choosing a key modulus greater than 512 may take a few minutes.
s1(config)#line vty 0 15
s1(config-line)#transport input ssh
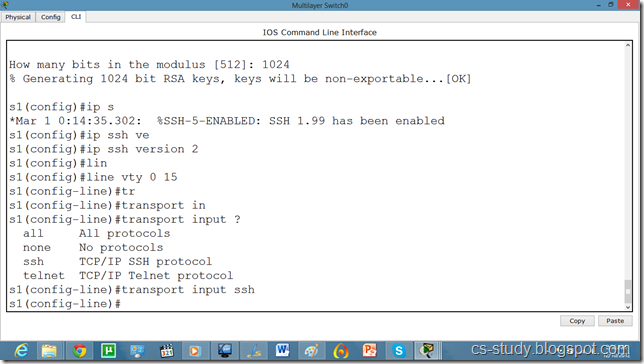
The name for the keys will be: s1.cs-study
How many bits in the modulus [512]: 1024
% Generating 1024 bit RSA keys, keys will be non-exportable...[OK]
s1(config)#ip ssh version 2
s1(config-line)#
Password Authentication Protocol on packet tracer (PAP)
The Point-to-Point Protocol (PPP) is a data link protocol commonly used in establishing a direct connection between two networking nodes. It can provide connection authentication, transmission encryption and compression. PPP is used over many types of physical networks including serial cable, phone line, trunk line, cellular telephone, specialized radio links, and fiber optic links etc. Internet service providers (ISPs) have used PPP for customer dial-up access to the Internet, since IP packets cannot be transmitted over a modem line on their own, without some data link protocol. PPP is commonly used as a data link layer protocol for connection over synchronous and asynchronous circuits, where it has largely superseded the older Serial Line Internet Protocol (SLIP) and telephone company mandated standards (such as Link Access Protocol, Balanced (LAPB).
PPP was designed somewhat after the original HDLC specifications. The designers of PPP included many additional features that had been seen only in proprietary data-link protocols up to that time.
HDLC
HDLC provides both connection-oriented and connectionless service. HDLC can be used for point to multipoint connections, but is now used almost exclusively to connect one device to another, using what is known as Asynchronous Balanced Mode (ABM).
A password authentication protocol (PAP) is an authentication protocol that uses a password. PAP is used by Point to Point Protocol to validate users before allowing them access to server resources. Almost all network operating system remote servers support PAP.
PAP transmits unencrypted ASCII passwords over the network and is therefore considered insecure. It is used as a last resort when the remote server does not support a stronger authentication protocol, like CHAP or EAP (the latter is actually a framework).
Password-based authentication is the protocol that two entities share a password in advance and use the password as the basis of authentication. Existing password authentication schemes can be categorized into two types: weak-password authentication schemes and strong-password authentication schemes. In general, strong-password authentication protocols have the advantages over the weak-password authentication schemes in that their computational overhead are lighter, designs are simpler, and implementation are easier, and therefore are especially suitable for some constrained environments.
PAP works basically the same way as the normal login procedure. The client authenticates itself by sending a user name and an (optionally encrypted) password to the server, which the server compares to its secrets database. This technique is vulnerable to eavesdroppers who may try to obtain the password by listening in on the serial line, and to repeated trial and error attacks.
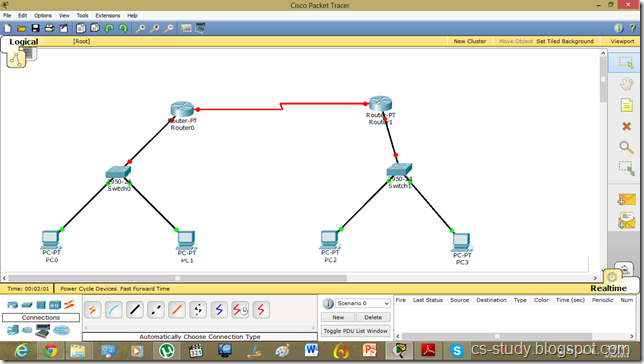
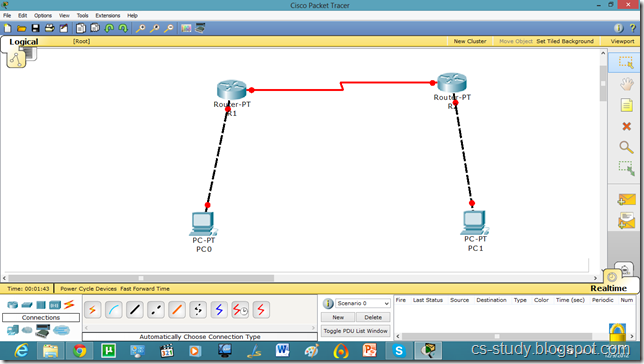
Let us apply PPP on packet tracer. Consider the following simpler topology.

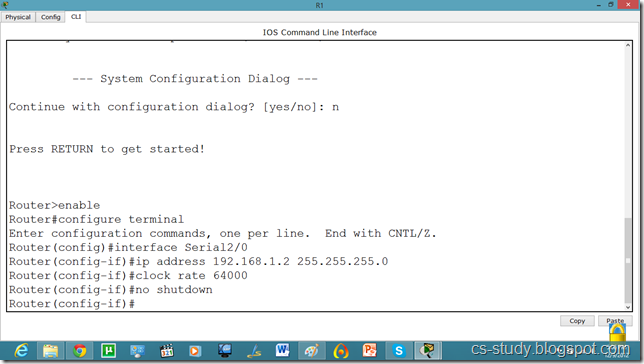
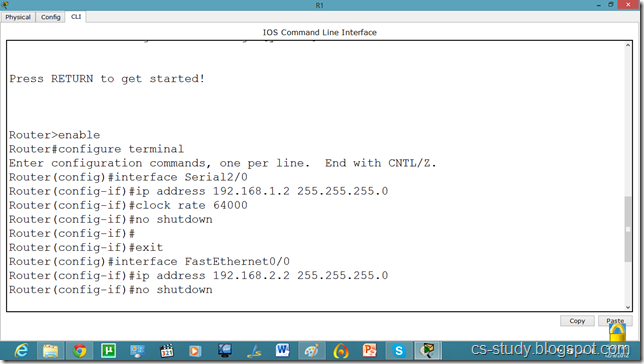
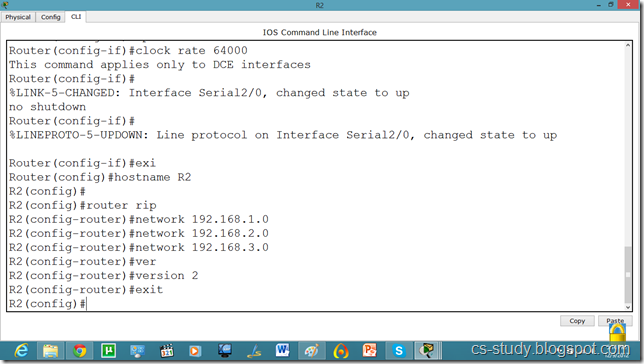
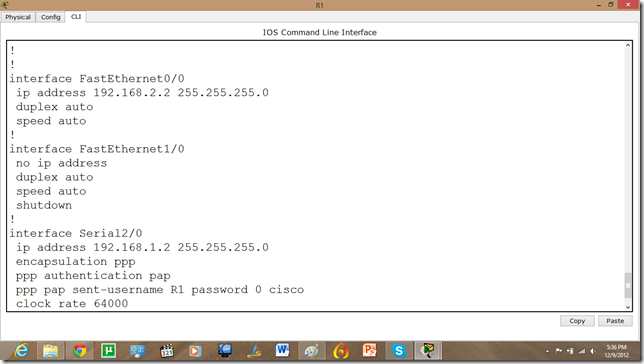
Let us apply IP addresses on the interfaces and change the state of the interface from down to UP. So that they can communicate.
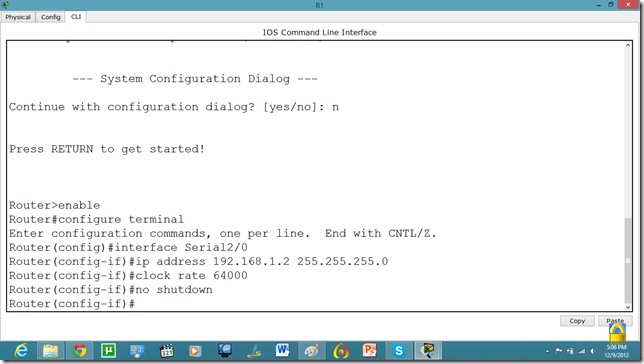
Similarly, for serial interface.
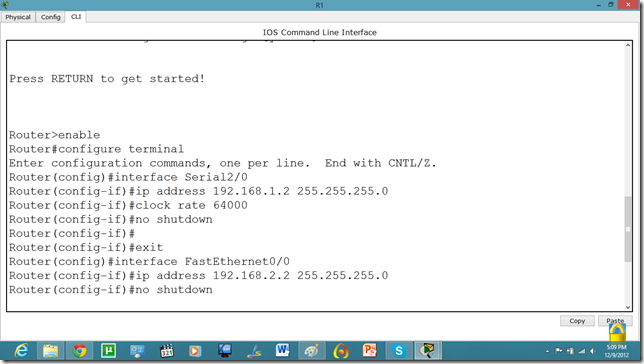
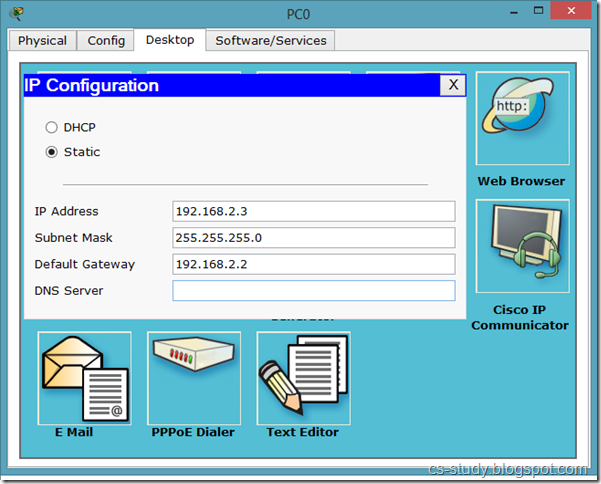
PC IP setup
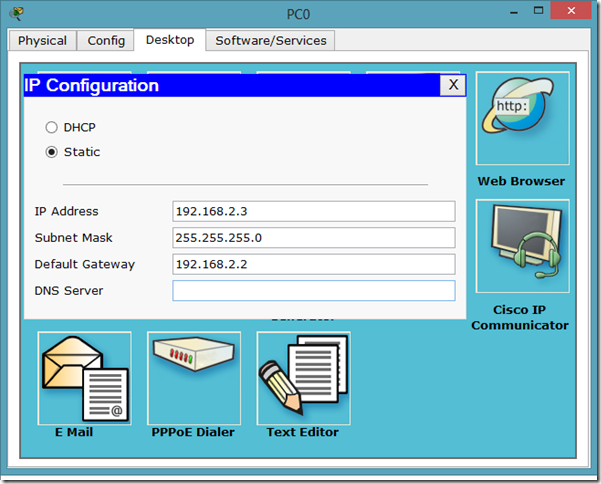
The IP configuration on other router.

serial int setup.
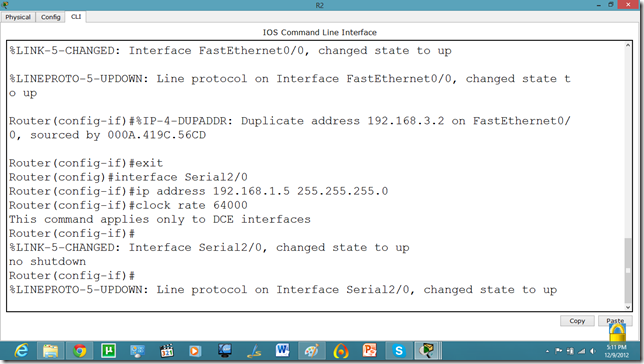
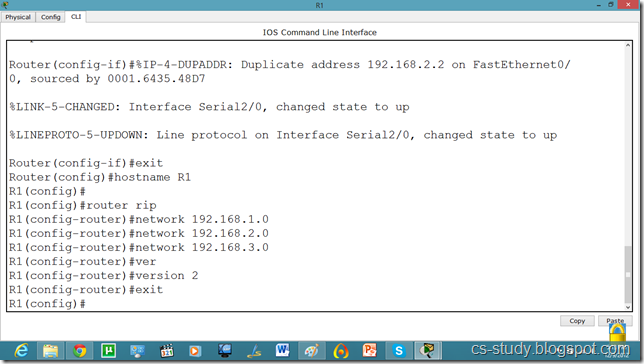
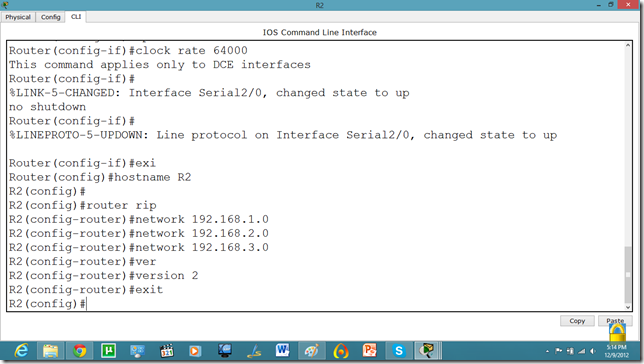
Now, we know that PCs that are attached cannot communicate until we apply a routing mechanism. In this case we are applying the RIP V2 protocol. Apply the following set of commands on both routers. We have also set the hostname of the router which will be useful to us later.
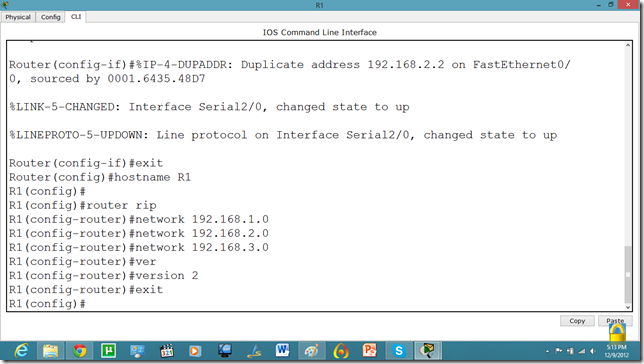
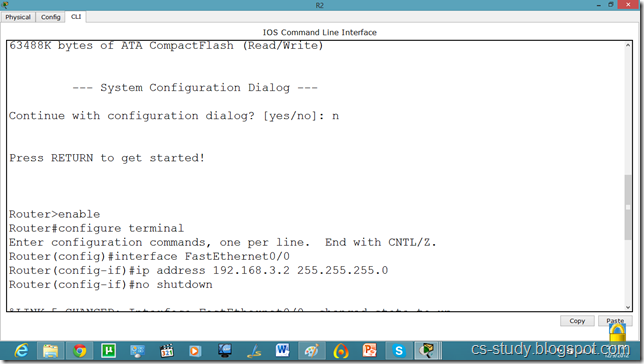
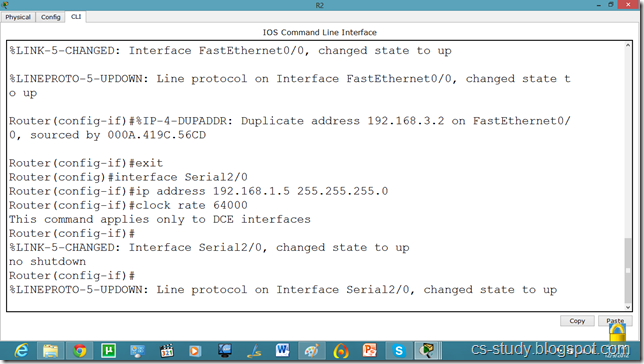
Now, let us set the commands on the second router as well.
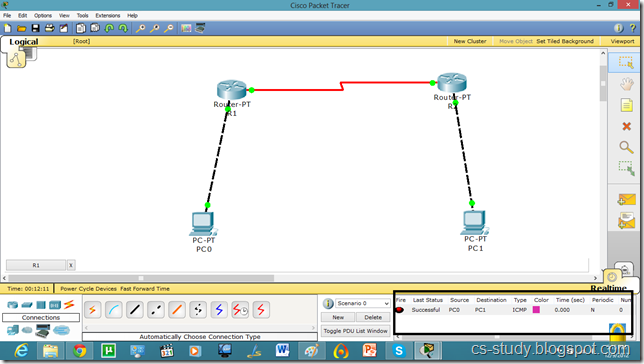
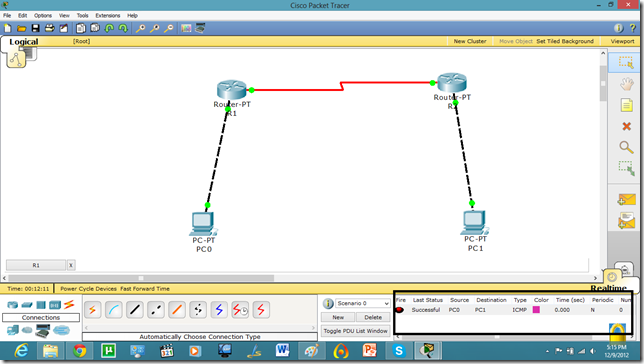
Now, both PCs can communicate.
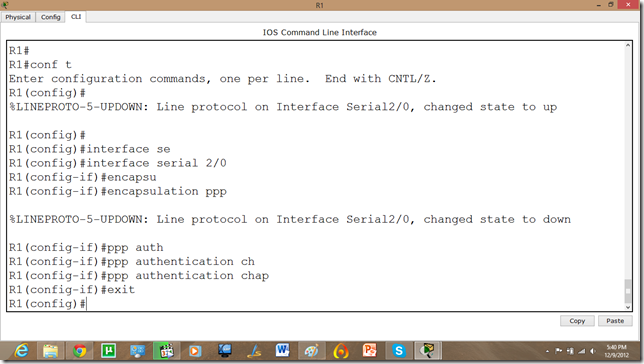
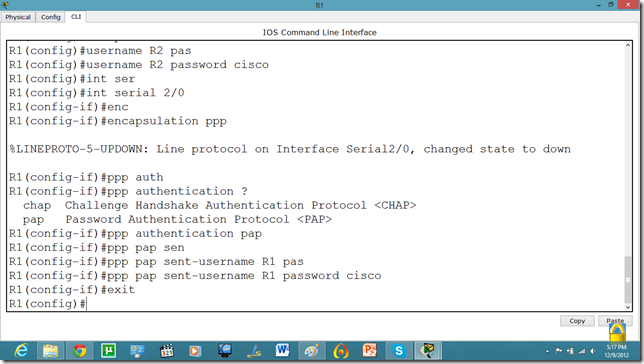
Now, we will set the authentication, In this tutorial we are going to apply PAP.
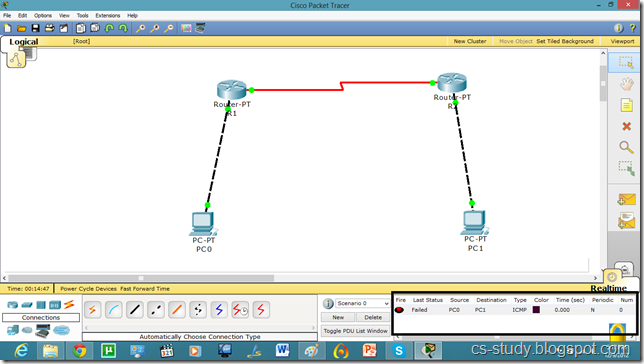
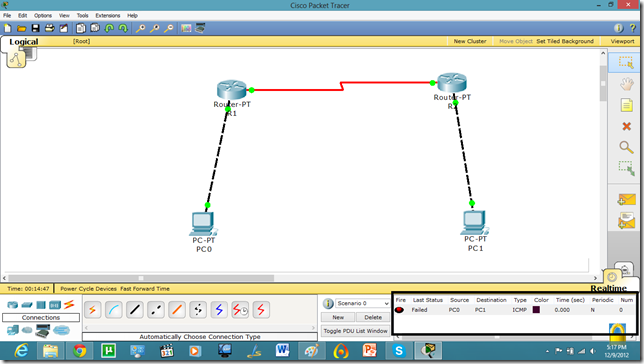
As we set the authentication on one router the communication is disabled.
Let us set it on other router as well.
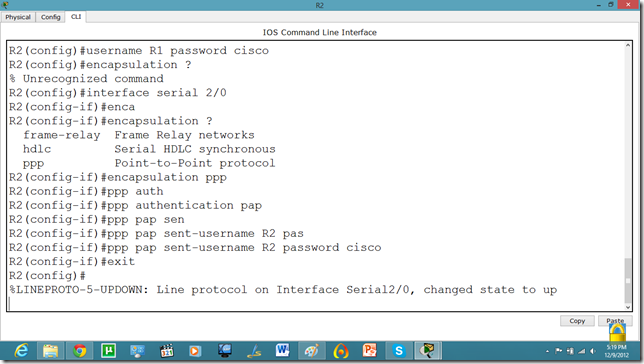
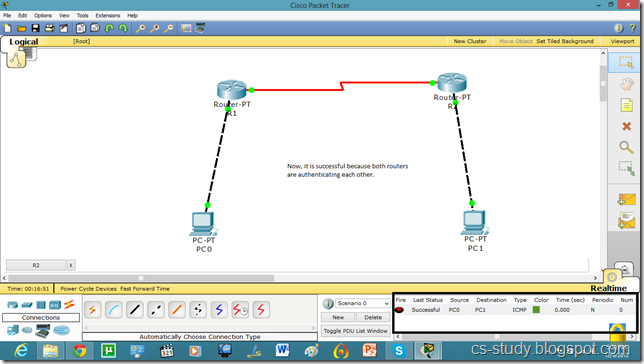
Now, they can communicate.
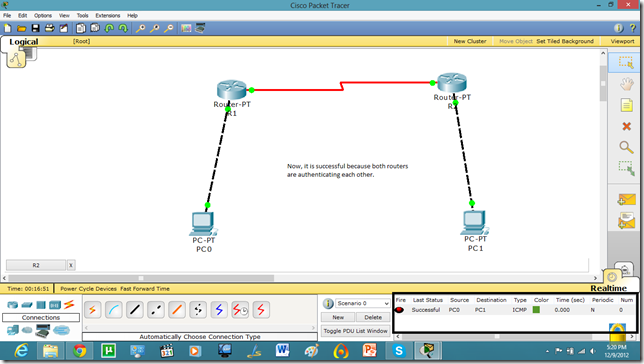
Now, if we run show run command in enable mode. We can see the authentication enabled in router.
Technorati Tags: packet tracer tutorial,pt tutorial,pap on packet tracer,ppp on packet tracer,password authentication protocol on packet tracer,password authentication protocol on pt,password authentication protocol,point to point protocol on packet tracer,point to point protocol tutorial,point to point protocol
Challenge Hand Shake Authentication Protocol on Packet Tracer (CHAP)
The Point-to-Point Protocol (PPP) is a data link protocol commonly used in establishing a direct connection between two networking nodes. It can provide connection authentication, transmission encryption and compression. PPP is used over many types of physical networks including serial cable, phone line, trunk line, cellular telephone, specialized radio links, and fiber optic links etc. Internet service providers (ISPs) have used PPP for customer dial-up access to the Internet, since IP packets cannot be transmitted over a modem line on their own, without some data link protocol. PPP is commonly used as a data link layer protocol for connection over synchronous and asynchronous circuits, where it has largely superseded the older Serial Line Internet Protocol (SLIP) and telephone company mandated standards (such as Link Access Protocol, Balanced (LAPB).
PPP was designed somewhat after the original HDLC specifications. The designers of PPP included many additional features that had been seen only in proprietary data-link protocols up to that time.
HDLC
HDLC provides both connection-oriented and connectionless service. HDLC can be used for point to multipoint connections, but is now used almost exclusively to connect one device to another, using what is known as Asynchronous Balanced Mode (ABM).
CHAP
CHAP provides protection against replay attacks by the peer through the use of an incrementally changing identifier and of a variable challenge-value. CHAP requires that both the client and server know the plaintext of the secret, although it is never sent over the network. The MS-CHAP variant does not require either peer to know the plaintext, but has been broken. Thus, CHAP provides better security as compared to Password Authentication Protocol (PAP).
CHAP Working
CHAP is an authentication scheme used by Point to Point Protocol (PPP) servers to validate the identity of remote clients. CHAP periodically verifies the identity of the client by using a three-way handshake. This happens at the time of establishing the initial link (LCP), and may happen again at any time afterwards. The verification is based on a shared secret (such as the client user's password).
- After the completion of the link establishment phase, the authenticator sends a "challenge" message to the peer.
- The peer responds with a value calculated using a one-way hash function on the challenge and the secret combined.
- The authenticator checks the response against its own calculation of the expected hash value. If the values match, the authenticator acknowledges the authentication; otherwise it should terminate the connection.
- At random intervals the authenticator sends a new challenge to the peer and repeats steps 1 through 3.
Another feature of CHAP is that it doesn't only require the client to authenticate itself at startup time, but sends challenges at regular intervals to make sure the client hasn't been replaced by an intruder, for instance by just switching phone lines.
Let us apply PPP on packet tracer. Consider the following simpler topology.
Let us apply IP addresses on the interfaces and change the state of the interface from down to UP. So that they can communicate.
Similarly, for serial interface.
And IP configuration on PC.
The IP configuration on other router.
Serial Interface setting.
Now, we know that PCs that are attached cannot communicate until we apply a routing mechanism. In this case we are applying the RIP V2 protocol. Apply the following set of commands on both routers. We have also set the hostname of the router which will be useful to us later.
Now, let us set the commands on the second router as well.
Now, both PCs can communicate.
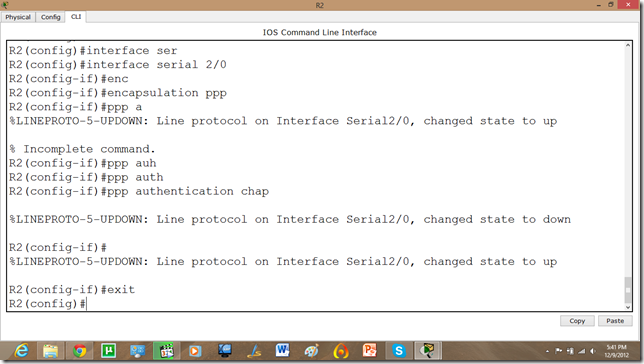
Now, we will set the authentication, In this tutorial we are going to apply CHAP(Challenge Handshake Authentication Protocol).
As we set the authentication on one router the communication is disabled.
Let us set it on other router as well.
Now, the communication is enabled.
Technorati Tags: packet tracer tutorial,pt tutorial,pap on packet tracer,ppp on packet tracer,password authentication protocol on packet tracer,password authentication protocol on pt,password authentication protocol,point to point protocol on packet tracer,point to point protocol tutorial,point to point protocol
Subscribe to:
Posts (Atom)
C program to Read From a File
#include <stdio.h> #include <stdlib.h> void main() { FILE *fptr; char filename[15]; char ch; ...
-
A terminal emulation program for TCP/IP networks such as the Internet. The Telnet program runs on your computer and connects your PC to a ...
-
Voice over IP (VoIP, or voice over Internet Protocol) commonly refers to the communication protocols, technologies, methodologies, and tra...
-
Star Formations http://cs-study.blogspot.com/2013/10/c-program-to-print-different-star.html Hollow...