A terminal emulation program for TCP/IP networks such as the Internet. The Telnet program runs on your computer and connects your PC to a server on the network. You can then enter commands through the Telnet program and they will be executed as if you were entering them directly on the server console. This enables you to control the server and communicate with other servers on the network. To start a Telnet session, you must log in to a server by entering a valid username and password. Telnet is a common way to remotely control Web servers. To telnet means to establish a connection with the Telnet protocol, either with command line client or with a programmatic interface.
SSH
Secure Shell (SSH) is a cryptographic network protocol for secure data communication, remote shell services or command execution and other secure network services between two networked computers that connects, via a secure channel over an insecure network, a server and a client (running SSH server and SSH client programs, respectively). It was designed as a replacement for Telnet and other insecure remote shell protocols such as the Berkeley rsh and rexec protocols, which send information, notably passwords, in plaintext, rendering them susceptible to interception and disclosure using packet analysis. The encryption used by SSH is intended to provide confidentiality and integrity of data over an unsecured network, such as the Internet.
a network protocol that ensures a high-level encryption, allowing for the data transmitted over insecure networks, such as the Internet, to be kept intact and integrate. SSH and SSH Telnet, in particular, work for establishing a secure communication between two network-connected computers as an alternative to remote shells, such as TELNET, that send sensitive information in an insecure environment.
In contrast to other remote access protocols, such as FTP, SSH Telnet ensures higher level of connection security between distant machines but at the same time represents a potential threat to the server stability. Thus, SSH access is considered a special privilege by hosting providers and is often assigned to users only per request.
Let us apply Telnet and SSH on packet tracer.
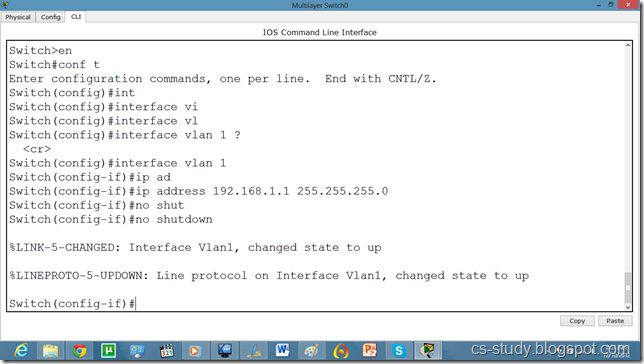
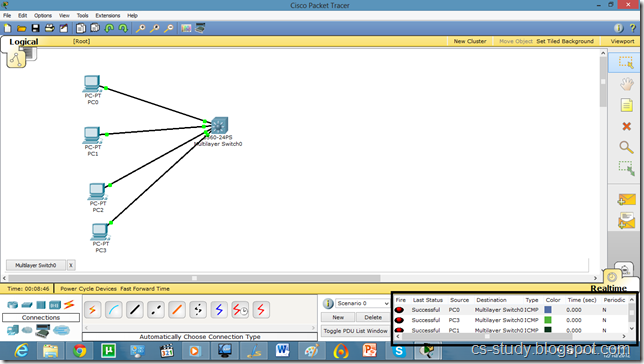
Take the topology as in the above diagram. Set IPs on the PCs. As, by default, all PCs are in vlan 1. We will create a virtual interface on switch with vlan 1 as follows.
Now, we can ping to switch by our hosts because hosts are in vlan 1 and switch also has a vlan 1 interface.
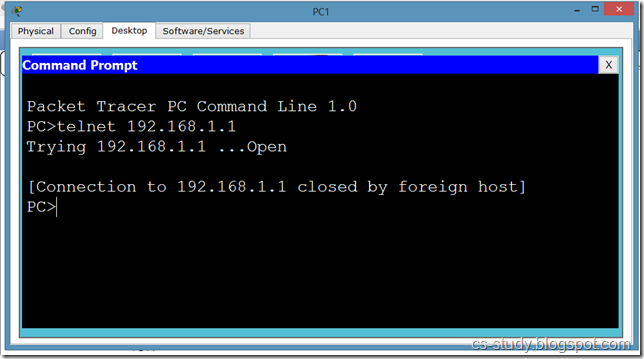
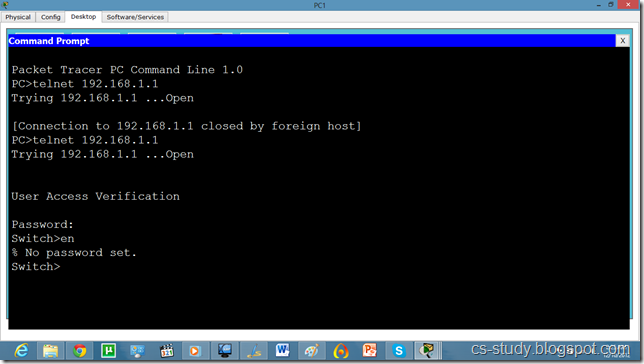
Now, try to telnet the switch from our PC, it refuses because we have not applied authentication on the switch yet.
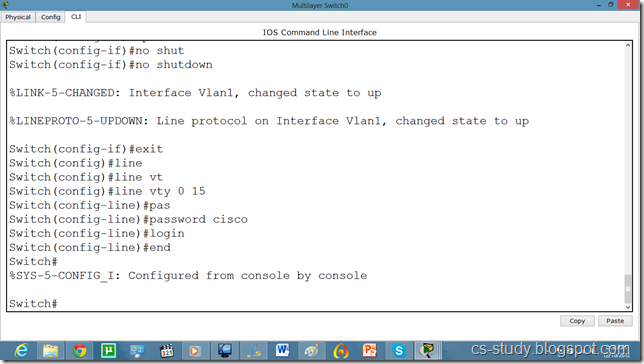
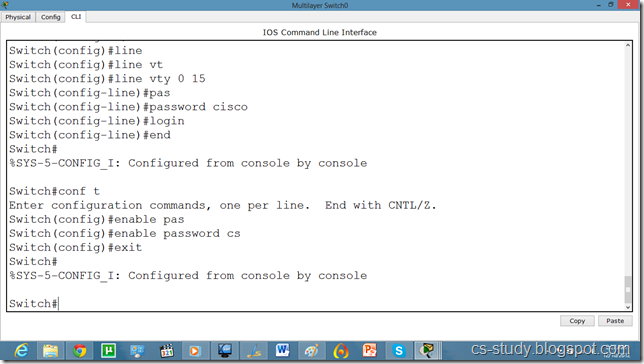
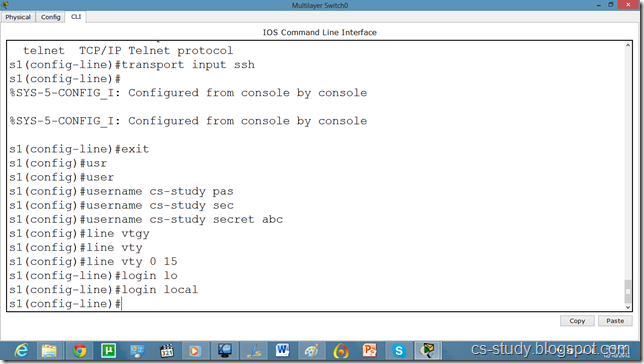
So, lets apply line authentication on the switch. The system supports 20 virtual tty (vty) lines for Telnet, Secure Shell Server (SSH) and FTP services. Each Telnet, SSH, or FTP session requires one vty line. You can add security to your system by configuring the software to validate login requests.
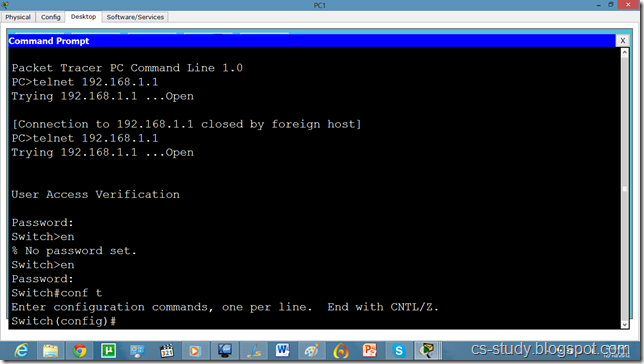
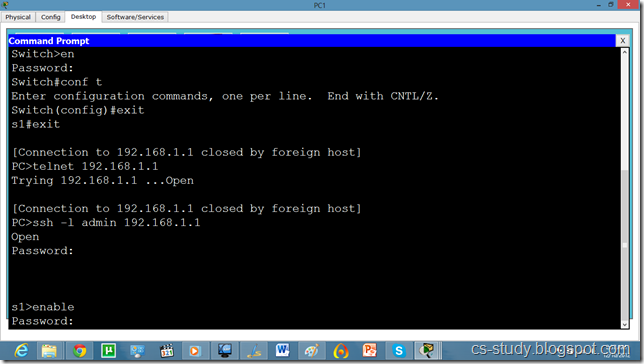
Now, we can easily telnet. But it does not let us go in the switch enabled mode because we have not set the password on the switch yet.
Lets apply password on the switch enabled mode.
Now, we can go inside Switch configuration mode from our pc.
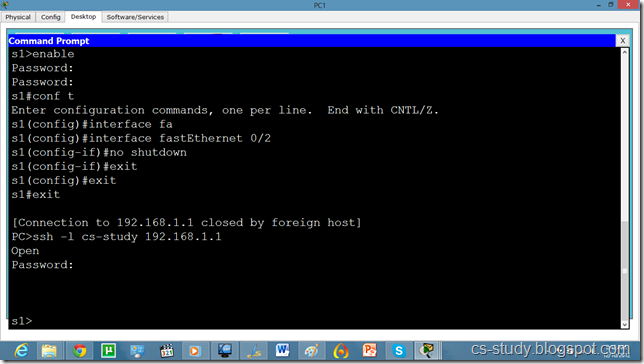
So, now let us apply SSH on the switch.
Commands continued.
Now, we try to telnet it but it is refused because ssh has over ruled telnet. So, we will use SSH protocol on it. By default username is admin.
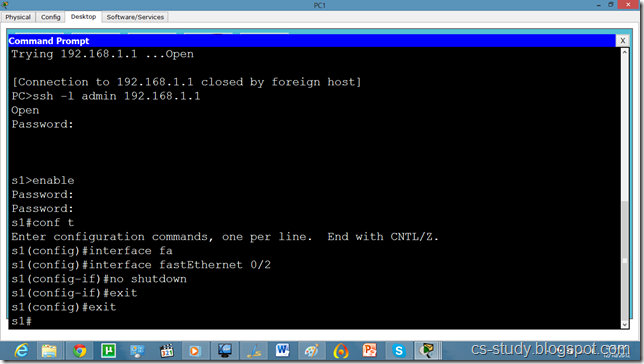
And we can apply any sort of configuration on our switch from out pc.
Now, if we want to change the username from admin to something else, we will do it as follows.
and from our pc as follows.
The SSH commands are as follows.
Switch(config)#ip domain name ?
WORD Default domain nameSwitch(config)#ip domain name abc.comSwitch(config)#crypto key generate rsa
% Please define a hostname other than Switch.
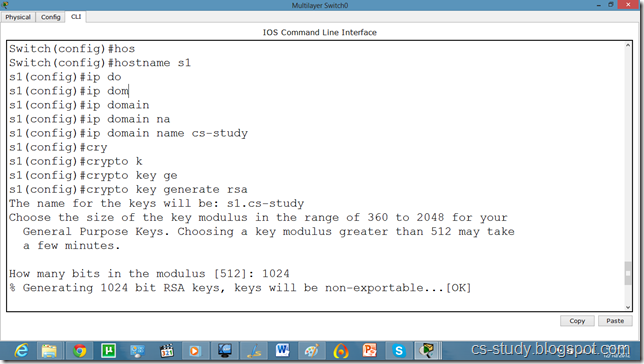
Switch(config)#hostname s1
s1(config)#ip domain name cs-studys1
s1(config)#crypto key generate rsa
Choose the size of the key modulus in the range of 360 to 2048 for your General Purpose Keys. Choosing a key modulus greater than 512 may take a few minutes.
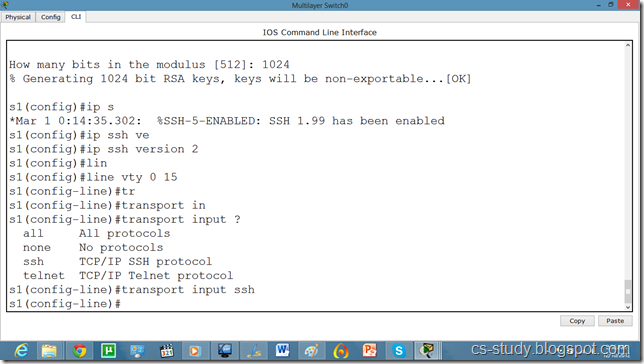
s1(config)#line vty 0 15
s1(config-line)#transport input ssh
WORD Default domain nameSwitch(config)#ip domain name abc.comSwitch(config)#crypto key generate rsa
% Please define a hostname other than Switch.
Switch(config)#hostname s1
s1(config)#ip domain name cs-studys1
s1(config)#crypto key generate rsa
Choose the size of the key modulus in the range of 360 to 2048 for your General Purpose Keys. Choosing a key modulus greater than 512 may take a few minutes.
s1(config)#line vty 0 15
s1(config-line)#transport input ssh
The name for the keys will be: s1.cs-study
How many bits in the modulus [512]: 1024
% Generating 1024 bit RSA keys, keys will be non-exportable...[OK]
s1(config)#ip ssh version 2
s1(config-line)#



nice
ReplyDeleteI just wonder what are the configurations in telneting multiple switches...can someone give me a full grasp?
ReplyDeleteyup thats possible. i have just tried that. Connect two switches with the crossover cable and attach PC to one of the switch. You can telnet both switches from that PC. Like in the image attached. PC0 is able to telnet both switches. Dont forget to provide the vlan interfaces to both switches in order to enable telnet. Hope that helps. Cheers :)
Deleteoops forgot to attach the url
Deletehttp://img585.imageshack.us/img585/8463/k8f.png
thankx it was really helpful
ReplyDeleteNice example, I doing a lab on packet tracer if possible to use teraterm with packet tracer.
ReplyDeleteNope, this is not possible. You will have to use the default PC command line.
DeleteCool!! thanks bro
ReplyDeleteNice information
ReplyDeleteThanks for sharing
Very useful information.
ReplyDeleteThank you.
How can a vlan interface be assigned a dhcp ip address??
ReplyDeleteHi , There is no DHCP applied here . Look carefully . DHCP is mostly applied either on router or Server. We rnt using any of those devices. We just applied IP address to vlan interface of switch so that we can ping the switch.
DeleteWorthwhile post on telnet and ssh on packet tracer and its effective working overall.
ReplyDeleteUseful and dynamic resource on post on telnet and ssh on packet tracer tools.
ReplyDeleteNice explaination very usefull..
ReplyDeleteSure thing bro!
ReplyDeleteThanks for using this blog its very helpful for solving router problems. Good work. Please visit this link……. Linksys Router Technical Support .
ReplyDeletehow can the beginners easily memorize the flow of configurations? advance thanks for answering this:)
ReplyDeletehow can the beginners easily memorize the flow of configurations? advance thanks for answering this:)
ReplyDeletehello,i don't know.why Laptop1 can't telnet to the switch0?
ReplyDeletehttp://www.packettracernetwork.com/packettracer53labs.html?id=16
Nice Share brother, keep sharing
ReplyDeleteAfter Configuring SSH on my switch, it cannot regonize enable feature any more, it just goes to the privillage mode straight away with out enable password, kindly help i may have done something wrong.
ReplyDeleteplease help
yow tru this one
DeleteR1>enbale
R1#conf t
R1(config)#enable secret
R1(config)#password cisco
R1(config)#login
R1(config)#line console 0
password cisco
R1(config)#line vty 04
R1(config)#pasword cisco
R1(config)#loginm
R1(config)#end
R1#copy running-config startup-config
i'm sorry MR. what the same configuration ssh you explain with ssh version 2.
ReplyDeleteGenuinely loved this kind of post. Although I want much more information on like precious subject matter.
ReplyDeleteToronto security cameras | Toronto Control4
This comment has been removed by the author.
ReplyDeleteI've been using another software for network diagramming and the diagram community consist of many examples. You can find more Cisco and network examples in creately diagram community
ReplyDeletegood, but you have forgot in the real network scenarios default VLAN (Vlan1) it's not recommended for security reasons, instead of create one else:
ReplyDeleteSwitch(config)# vlan id_de_vlan
Switch(config-vlan)# name name_of_vlan
Switch(config-vlan)# exit
Switch(config)# interface interface_id
Switch(config-if)# ip address 192.168.1.1 255.255.255.0
Switch(config-if)# switchport access vlan id_de_vlan
and then the rest of settings.. as VTY security, etc..
Very informative and well written post! Quite interesting and nice topic chosen for the post.
ReplyDeleteonline baccarat
สูตรบาคาร่า
baccarat
Really have good to know this information .Thanks for sharing.Keep posting...
ReplyDeleteD38999 connectors
Nano-D connectors
This is exactly what I was searching for. Awesome post. Thanks a bunch. Helped me in taking the class for my students. Wish to follow your posts, keep writing! God Bless!
ReplyDeleteBest Selenium Training Institites in Kalyan Nagar Bangalore
ReplyDeleteThere is a great importance of Web Design & Social Media for Businesses. Everybody knows how important social media is for businesses and web designs these days. In order for any business to be successful, establishing a social media strategy is essential. Part of the strategy should include website design.hosting webmaster visit: https://www.bynd.co.in
ReplyDeleteIn Chau Long We are proud to bring our customers the products of printing paper bags, printing paper boxes, printing catalogs, printing directories, printing leaflets, high quality printing leaflets, reasonable prices and Meet all requirements for the customer's process set.
In vỏ hộp đựng giày
In hộp đựng rượu
in vỏ hộp
in offset hà nội
Mesmerized article written on this blog with other relevant information. It is straight to the point that how we can improve our skills as well as how we can be represented to a new stream of professionalism.
ReplyDeleteAcer AT350 F3
Good Post! Thank you so much for sharing this pretty post, it was so good to read and useful to improve my knowledge as updated one, keep blogging.
ReplyDeleteInternet Of Things training in electronic city
You can also refer to different types of online tools which consist different diagrams and templates which you can select to draw your Cisco, IT and Network diagrams.creately engineering solutions
ReplyDeleteYou have ended my 4 day long hunt! God Bless you man. Have a great day. Bye
ReplyDelete타이마사지
I have read a few of the articles on your website now, and I really like your style of blogging. I added it to my favorites blog site list and will be checking back soon. Please check out my site as well and let me know what you think.
ReplyDeletetag protocol crypto
I liked the writing about such a niche service. In the modern era, it is hard to discover great articles.
ReplyDeleteCustom Software Development
A debt of gratitude is in order for posting this information. I simply need to tell you that I simply look at your site and I discover it exceptionally fascinating and educational. I can hardly wait to peruse bunches of your posts. dormire meglio la notte
ReplyDelete